We deliver services in:
Working Hours:
M-F: 8AM-7PM / S: 10AM-4PMNeed Urgent Support?


A sudden system slowdown. Unexplained logins. Ransomware notes.
If you’re seeing signs of a cyberattack, time is critical.
Our Digital Forensics and Incident Response (DFIR) team is here to help you take back control—fast.
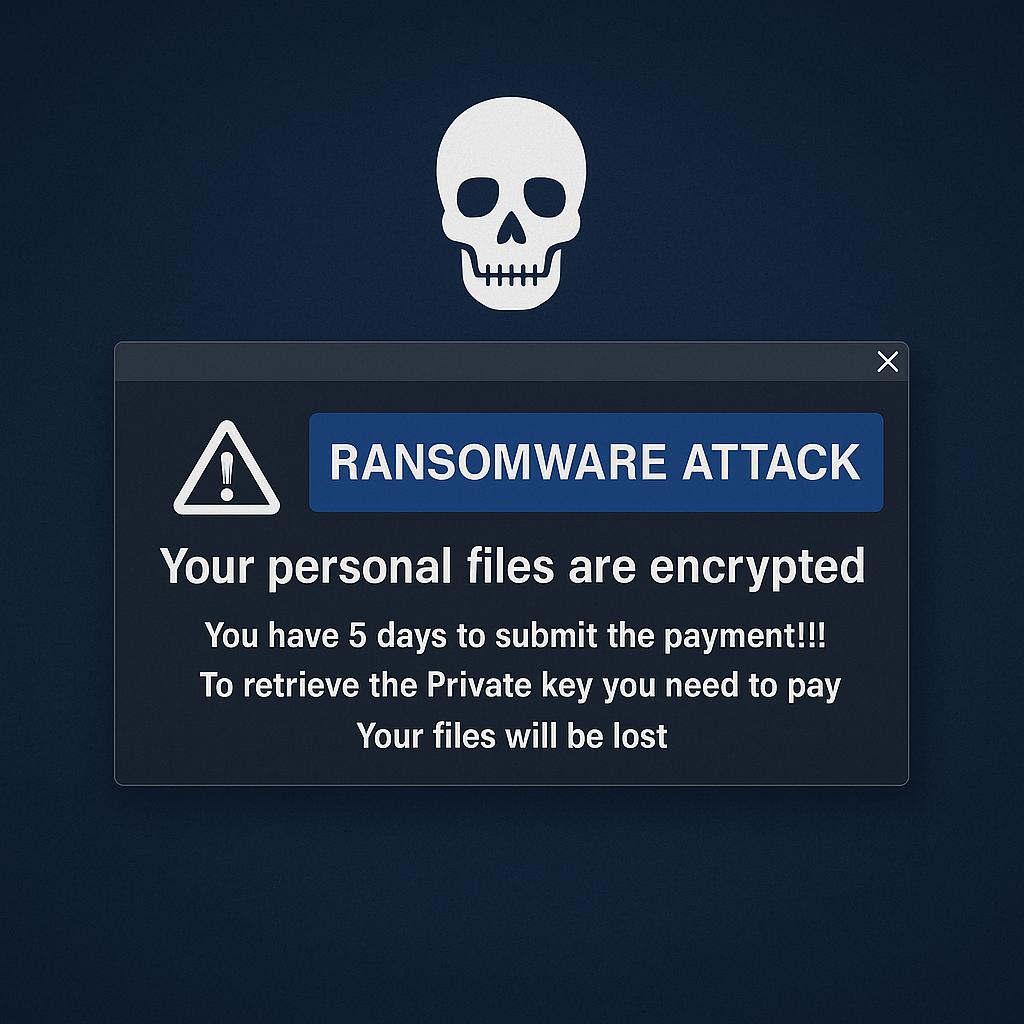
Digital Forensics and Incident Response (DFIR) is the practice of identifying, investigating, containing, and remediating cybersecurity incidents. It combines the technical precision of forensics—the collection and analysis of digital evidence—with the speed and strategy of incident response, which involves neutralizing threats in real time and minimizing damage. Whether it's a ransomware attack, insider threat, phishing campaign, data breach, or system compromise, DFIR helps your organization understand WHAT happened, HOW it happened, and HOW to prevent it from happening again.
Get full visibility with executive and technical reports.
We quickly assess what's happening, what's affected, and how to respond.
We stop the spread, isolate compromised systems, and remove all malicious activity.
We dig deep to uncover: How the attacker got in? What they did? What data was accessed? Who may be responsible?
We secure, rebuild, and restore your systems—without disrupting your business.
DFIR stands for Digital Forensics and Incident Response. You would need DFIR services if your organization has experienced a cybersecurity incident, data breach, insider threat, or suspected compromise—we investigate, contain, and help recover from such incidents.
We offer rapid response services and can often begin containment and investigation within hours. The faster we’re involved, the more likely we can minimize damage and preserve crucial evidence.
Yes, identifying the attack vector is a core part of our forensic investigation. We analyze logs, memory, disk images, and network activity to determine how the breach occurred and what data may have been accessed or stolen.
Absolutely. We provide detailed forensic reports that can be used for legal proceedings, compliance (e.g., GDPR, HIPAA), insurance claims, and internal audits.
Yes, once the immediate threat is addressed, we work with you to strengthen your defenses through incident response planning, endpoint monitoring, threat hunting, and cybersecurity awareness training.
Round-the-clock availability to respond to incidents and contain threats without delay.
Our team includes GCIH, GCFA, CISSP, and OSCP-certified professionals with real-world breach experience.
Get thorough, legally sound reports ready for use in compliance, litigation, or law enforcement cases.
Your incident is handled with complete confidentiality, integrity, and minimal business disruption.
From lean tech teams to global corporations, clients trust us to safeguard what matters most.

© Nxt Door Technology. All Rights Reserved by Nxt Door Technology